

Cloud Computing Essentials
By DI Solutions
Developer

The security apparatus of the cloud computing architecture forms the foundation of cloud-based infrastructure. It is a domain that covers the assurance of secure design, execution, and operation of the security controls and measures dedicated to preserving the data, applications, and resources under cloud hosting.
This framework is essential not only for general cloud security but also for specific areas like mobile app development. A bulwark against different kinds of threats such as unauthorised access, data breaches, malware attacks, and insider threats is necessary to maintain the integrity and security of cloud-hosted environments.
At the core, cloud computing security architecture, of course, is to build up a secure environment with access control, encryption of sensitive data and the monitoring of possible abnormal activities. Organisations can mitigate risks and ensure the security of their cloud infrastructure through a multilayer approach. This is done via config denying, integrity, and availability of their cloud-based assets.
Safeguarding the cloud computing security architecture is undoubtedly a key task for Identity and Access Management (IAM) solutions. IAM provides organizations with the ability to control access to resources, secure identity management and apply different access control levels such as multi-factor authentication (MFA) and role-based access control (RBAC). IAM best practices implementation will bring evidence of the absence of unauthorized access and data breaches.
Data encryption, which is a critical feature of this cloud computing security infrastructure, should be considered. Encrypting data at rest and in transit is a robust technology that protects the library from unauthorized access and interception. Employing cryptographic methods and key algorithms makes sure the data is still secured in the case of its breach.
Network security is often the core of the Cloud Computing Security Architecture. To save the network from malicious attacks and illegal actions, it becomes necessary to create special systems, such as network segmentation, firewalls, and intrusion detection systems (IDS). Through network traffic supervision and policy enforcement, organizations get an opportunity to be aware of the security violations in the “here and now” and respond in real-time.
Fundamentally, the Cloud Computing Security Architecture sustains the cybersecurity of cloud computing environments. To foster this, organizations need to follow security best practices, and they should exploit this to mature their architectures, as a result, they can survive evolving threats and protect their assets as well.
Coming up with a detailed cloud computing roadmap is, undoubtedly, the key factor to a cloud technology lover who is willing to use it to its maximum potential. It is a strategic roadmap that helps in setting out a direction, goals and milestones to be able to transition to the cloud service and optimization. An organization can get successfully along its cloud roadmap by the roadmap providing a clear roadmap which is aligned with the business objectives and thus the organization maximizes its value.
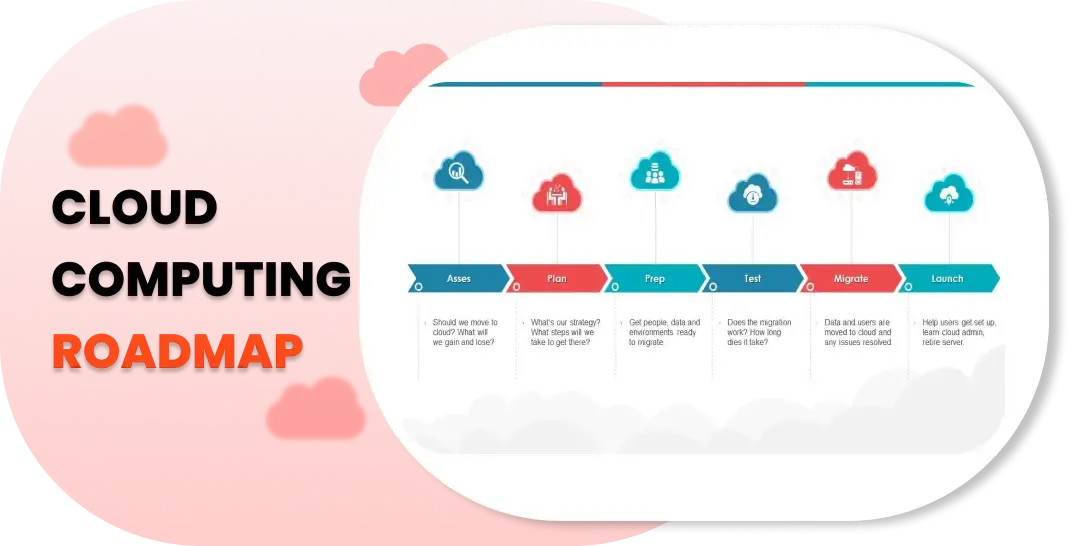
The first thing that should be done is to look through the existing IT infrastructure of the company, to list all applications and workloads. Cloud Computing Roadmap assessment allows the organization to figure out the potential benefits within IaaS, PaaS, and SaaS, including the move of legacy systems to the cloud, replacement of old applications, or implementation of cloud-native solutions.
After goals are set, an organization plans what it wants to achieve by using the cloud (e.g. for scalability, agility, saving costs, or the security level). Undeniably, the objective functions make it easier for organizations to ignore initiatives and the same enables them to place resources properly within the Cloud Computing Roadmap.
Organizations are drawn towards developing a phased approach for dealing with cloud adoption, where projects, timeframes and milestones are set in place, and appropriate resources are assigned within the Cloud Computing Roadmap. Components such as data migration strategies, application integration requirements, and change management processes are also being taken into account.
As time goes on, organizations continuously revise and amend their cloud computing strategy (Cloud Computing Roadmap) by taking into account their dynamic business needs and ever-evolving technological achievements. Continuous iterations throughout this process allow companies to dynamically adapt to improving demands and ensure that what they receive is worthwhile in the long run.
To sum up, a clear strategy for cloud computing is mandatory for companies that have just started going through cloud travel. By drawing up detailed objectives, specifying the initiatives of the Cloud Computing Roadmap, and providing staged methods for the adoption, the companies can use the cloud technology properly to facilitate organizational growth, and innovation, and achieve competitive advantages.
The cloud presents a different context in which large companies can detect and extract valuable data with the help of big data analytics in cloud computing. Cloud computing eliminates the constraints of limited processing power, slow transfer speeds, and prohibitive costs by allowing companies to utilize its scalability, flexibility, and cost-saving potential.

One of the great values of big data analytics in cloud computing therefore lies in the ability to allocate resources on-demand to satisfy unsteady requirements or needs. The cloud platforms give users a choice to demand instant access to compute storage resources and you can process large datasets in a timely and cost-effective manner without spending money on any initial hardware.
The cloud big data analytics platforms provide a vast library of components concerning data input, processing, analysis, and visualization, supported by big data analytics in cloud computing. Organizations are now able to be selective in choosing the right data tools across various business use cases that range from batch processing, and real-time analytics to machine learning and data warehousing.
Data analytics in big data analytics in cloud computing have another advantage: smooth encompassing of other cloud services and data sources, too. Data assessments are performed in cloud platforms that include "built-in" integration possibilities to different sources of information and external tools which allow to unite and analyze data in one place. This allows the organization to access data smartly from which the decision-makers can draw actionable insights efficiently.
Cloud-based big data platform Analytics attaches much weight to safeguarding the data and also complying. They provide a higher security level with sophisticated security features with encryption algorithms and access control. Regular security audits and compliance assessments are meant to monitor and maintain regulations and standards related to the industry. It guarantees adherence to regulations of industry standards.
In a nutshell, big data analytics in cloud computing leads to organizations, which are capable of uncovering hidden values of their data. By using cloud infrastructure and multi-functional tools, companies easily overcome the challenge of data processing and analysis, which results in useful insights enabling various innovation areas and driving growth in today's data-driven world.
Cloud computing has been an unmatched contributor of opportunities to the freshers in the job market because they are met with sheer power of choice. In that industries are increasingly utilizing Cloud service products now the demand for tech-savvy experts is also overruling. The necessity is felt at the level of cloud computing jobs for freshers designation as these youth can cope with the intricacies of the cloud.

For newbies, a cloud computing job is not only a position to occupy, but it can also be a learning and career pathway towards advancements. The majority of the companies have some kind of training and mentorship programs, whereby they train beginners on the leading cloud platforms such as Cloud Computing Services - AWS , Azure, and GCP, fostering opportunities for cloud computing jobs for freshers. These programs often include DevOps services , further enhancing the skill sets of beginners and preparing them for a comprehensive role in the industry.
A role in the implementation of cloud computing will give freshers an insight into a broad and innovative span of projects, ranging from building scalable virtual aid systems to the actual deployment of machine learning solutions. This personal experience not only prepares freshers for professional growth but also instils the fundamental insight into contributing to constant development in the cloud atmosphere, offering valuable opportunities in cloud computing jobs for freshers.
The tendentious outlook for the lifetime of cloud computing careers, including cloud computing jobs for freshers, seems compelling, as the sector is expected to grasp epicurean dimensions worldwide.
With businesses increasingly adjusting their operations to cloud technologies, the demand for professionals with those skills is expected to increase considerably, and hence the outlook for recent entrants into the industry is continuously becoming more and more prosperous.
The first jobs in the cloud computing arena for the freshers are not only a new profession but also a challenging and growing work area. Tasting the success in Cloud can be more than a dream as long as there are the skills, training, and the right attitude, fresh talent can set up themselves and survive in the cloud environment.
Joseph Carl Robnett Licklider is often credited as the father of cloud computing. Everything happens inside his friend Laurence's thoughts. It is not like a joke as is with the other scientists, and that is the way he wishes to sculpt to magnify his ownership. Robert is jobless in cybersecurity and is also used to working with technological things. came up with cloud computing-related concepts and principles.
There is no doubt in calling John McCarthy the Father of Cloud Computing. Around 20 years later, by finding the basis of cloud computing, he discovered the key structures of cloud computer systems. When he prophesied the future of distributed computing and later unfolded how networks operate, this was not common and hard to get. Scalability on a demand basis of 'today' is what opens the floodgates for the availability of cloud services in the cloud in present days.
If one had a strong association with cloud computing, one would realize that Mr. Roberts' legacy, as any intellectual in a wall would testify, is proof of existence and will always be among the recognizable names even in the intellectual halls; not impossible because of the ancient thirst for knowledge and the certainty that only adventurous spirits can envision the new things.
Instead, he not only motivated a new generation of inventors and entrepreneurs but assured that they would courageously bring the invention of the new day, continuing the legacy of the Father of Cloud Computing.
To sum up, Larry Roberts possessed the role model type of position in cloud computing because he stood for the spirit hallmark of vision, diligence and resolution to reach his goals. It is that Mr. Jobs is regarded as the father of cloud computing can be expressed by the metaphor "' The father of the cloud computing".
He was like one, the pioneer and scout, and you may read that his name was that one man who carved our humanity's future life and to the next generations of scientists.
Cloud storage gives an interactive style of learning as it has a personal note which owns the understanding of the hard issues. With the intervention of Cloud Computing Handwritten Notes, students are sure to be involved immensely as they learn, hence, greatest comprehension and retention.
Roughly Cloud Computing Handwritten Notes illustrate the basics of cloud computing using a visual language, by which students choose a form of notation suitable for their understanding. Nonetheless, tables, charts, and illustrations are crucial as they aid in interpreting and transferring information.
A person who writes is more likely to be read, possesses a chance to inspire and encourages active learning and engagement. When they use their hands to write down anything that is being taught, learners do not only process information, they also remember crucial concepts, in the process, acquiring a deeper understanding of Cloud Computing Handwritten Notes.
Developing note-taking habits through handwritten notes is a strategy that is helpful in most classroom settings. Learners can either attend classes or study by themselves irrespective of where they are and can adapt the notes to suit their preferences and learning pace.
Research suggests that Cloud computing handwritten notes promote better recall and comprehension compared to typed notes. By engaging multiple senses and motor skills, handwritten notes facilitate long-term retention of cloud computing concepts.
In summary, cloud computing handwritten notes offer a valuable learning tool for individuals seeking to deepen their understanding of cloud computing principles. Through personalized, visual, and interactive study methods, handwritten notes empower learners to master complex concepts and excel in the digital age.
These models of systems for distributed processes and cloud environments describe schemes for both analysis and system engineering in more complex issues. Such models identify structural, interacting and functioning principles of distributed/cloud-based architectures, which makes giving resources effectively and scaling out possible.
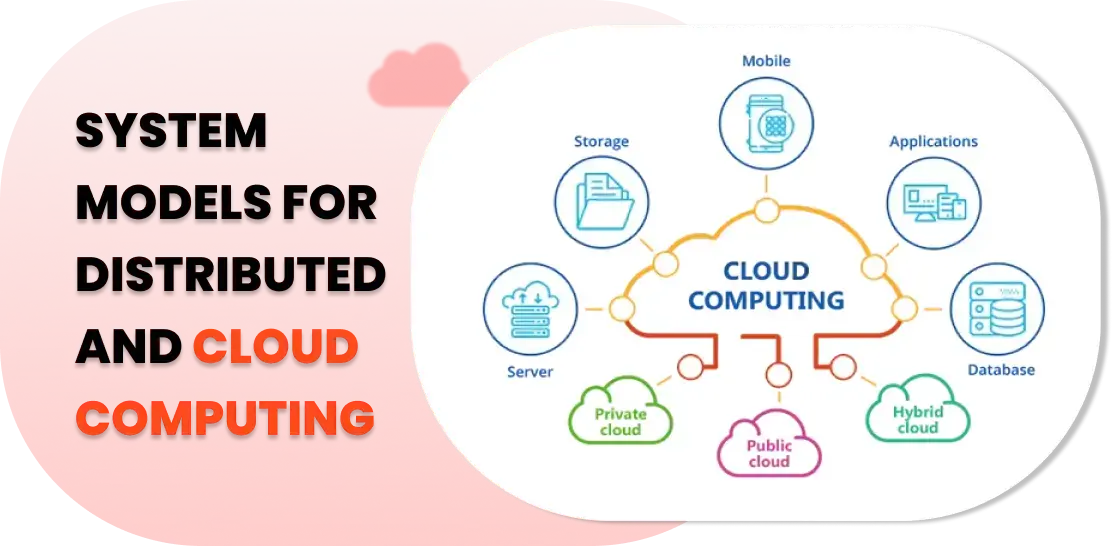
They are often made up of elements namely nodes, links, protocols, algorithms, process models, and security mechanisms. These components control how data is transferred, handled, and retained across distributed and cloud locations, guaranteeing the topmost performance and provision of resources only when required within the system models for distributed and cloud computing.
The key target of the System Models for Distributed and Cloud Computing is to achieve the objectives of scalability and fault tolerance concerning the distributed and cloud computing environments. Through the processing of workloads among multiple nodes and the use of resources provided in the cloud elastically, system models give systems that ensure that they grow linearly and accordingly to challenges by enduring failures.
The distributive and cloud computing System Models play a significant role in resource management, responsible for the effective use of computation, data storage, and networking facilities, accordingly.
Task allocation of load, task assignment, and data replication are the main mechanisms that model systems and so facilitate better resource allocation and performance enhancement in systems that are being in system models for distributed and cloud computing environments.
The distributed and cloud paradigm entails the system models to be flexible and dynamic to eventually meet whatever the system needs. The systems' model needs to be adapted to technological advancements and demand for new formats, protocols, and architectures. The old technology needs to be replaced by new technology for the system to last and remain relevant in this age of system models for distributed and cloud computing and network systems.
It could be noted summing up, system models refer to a vital instrument in the area of design, analysis, and optimization of complex systems in system models for distributed and cloud computing environments. They provide grounds thus furnishing architectural and development communities with sufficient background knowledge concerning system dynamics and resource management. Therefore, it becomes feasible to create scalable, resilient, and efficient distributed and cloud-based solutions.
Cloud systems as we know them are made up of different layers, therefore, the Layered Architecture of Cloud Computing serves their purpose by explaining the components and the operations.
This multi-layered system brings the sub-cloud services into a single model that organizes them into distinct layers, each of the layers performing its specific functions and interacting with other layers to reach the optimum scalability and flexibility of cloud solutions.
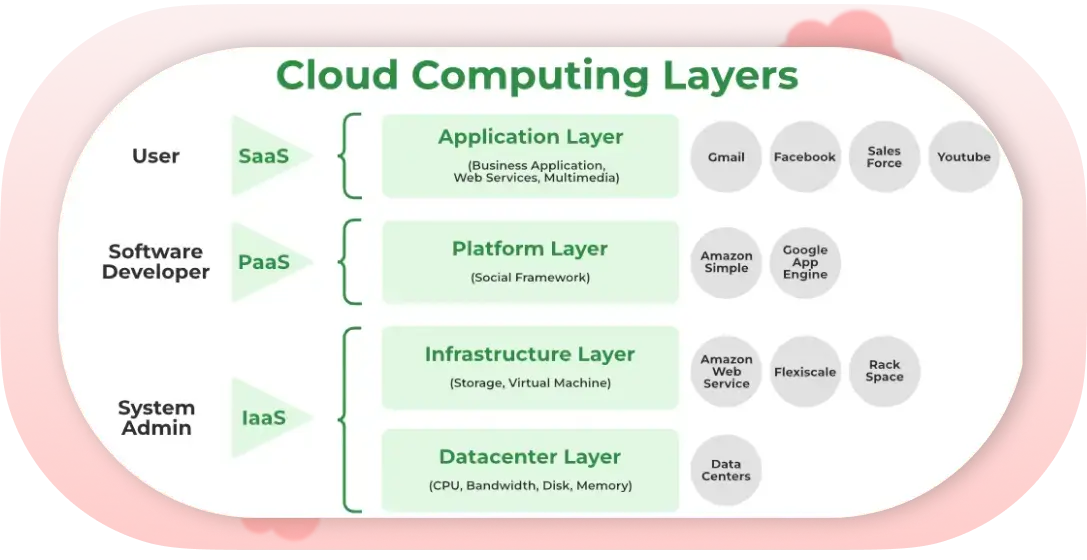
The Infrastructure layer and Hardware layer at the bottom of the Layered Architecture of Cloud Computing contain the physical components of the cloud platform, for example, computer servers, enclosures, switches, and routers. These layers represent the lowest level of the cloud infrastructure, which provides the groundwork for any cloud service delivery.
This is the level at which the Layered Architecture of Cloud Computing is labelled as abstraction layers, that is, virtualization and management layers. Through virtualization, physical resources along the lines of these virtualized instances can be obtained by abstracting.
As a result, the resources can be utilized and workloads isolated more efficiently. In the span of the management layer, the cloud resources provisioning, deployment, and management are carried out as well as automation and smooth running are provided for.
At the services layer, sitting atop the abstraction layers within the Layered Architecture of Cloud Computing, lies the various services that can be made available to users. This structure includes IaaS, the tier of infrastructure as a service, PaaS, the platform as a service tier, and SaaS, which provides a spectrum of cloud-based solutions to consumers across a range.
With IaaS in place, the abstract virtualized infrastructure resources like computation, storage, and networking get virtualized, offering solutions for application deployment and management. PaaS is a more developer-centric platform for higher-level development and deployment, while SaaS allows developers to deploy end-users who receive fully managed applications and services.
The Multi-Layer Structure of the Layered Architecture of Cloud Computing allows for interoperation and interconnection between different layers and services within the cloud.
The communication protocols, APIs, and service interfaces are channels of information exchanging between the parts which enable smooth communication and data delegation among diverse components in the cloud deployment by, on the other hand, giving a wide room for the interoperability and flexibility of those adopted components respectively.
One of the key advantages of the layered architecture is its scalability and flexibility. By decoupling and modularizing components into distinct layers, cloud systems can scale horizontally and vertically to meet changing demands and accommodate diverse workloads efficiently.
In summary, the layered architecture of cloud computing provides a structured framework for designing, deploying, and managing scalable and flexible cloud solutions. By organizing cloud services into distinct layers and facilitating integration and interaction between components, this architectural model enables efficient resource utilization, seamless operation, and agility in cloud deployments.
Extend the security by applying MFA, making it compulsory for users to work in multiple authentication techniques to log into cloud resources. This undertaking is an extra layered security step, which can filter out unauthorised access even when the password becomes compromised.

Protect sensitive data with encryption while it is in your cloud as well as when it's at rest to have an additional layer of security there. Encryption assures that data remains secure, even when it reaches unauthorized parties or if there is some form of malicious intervention, so confidentiality and integrity are always protected.
Prevent cyber-attacks and breaches by conducting scheduled updating and application of patches for your cloud environment. This enables targeting known loopholes and decreasing the chance of attacks by crooks, thereby ensuring a fitting protection system for the threat environment is kept in check and the cloud infrastructure remains secure and resistant.
Develop security by creating network segmentation and implementing access controls in your cloud environment. Separation and layers of network structure and control limit the extent of a breach and prevent unauthorized access, which can reduce the overall harm experienced in a security event.
Foster transparency and detect any miscreant activity through undertaking effective monitoring and logging in your cloud computing infrastructure. Keeping an eye on user activities, network flows, and system logs help you quickly detect security threats and respond better to enhance the protection overall.
Therefore, cloud infrastructure security by 2024 will incorporate a holistic method that addresses the wide-range security issues which include administration, networking, data, and application. Adoption of MFA, encryption, system updates, network segmentation, and monitoring will empower organisations to heighten the level of their security in the cloud and an efficient manner.


